OAuth, SAML and OpenID Connect
OAuth 2.0 is an authorization framework, not an authentication protocol
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
+-------------+ +------------------+
| |--(1) Auth Request------------>| Authorization |
| | (openid scope) | Server |
| | | (e.g., Google) |
| User/Browser|<-(2) Login & Consent----------| |
| | +------------------+
| |--(3) Authorization Code------->| |
| | | |
| |<-(4) ID Token + Access Token--| |
+-------------+ +------------------+
|
| Use ID Token to identify user
|
v
+-------------+
| Your App |
| (verifies |
| ID Token) |
+-------------+
At the risk of over-simplification, OpenID Connect is a rewrite of SAML using OAuth 2.0
- OIDC is essentially an extension of OAUTH 2.0.
OKTA
Integration Network
Experiment.
- Register an account. Must use a company email.
- Add a user with personal email.
- Then two urls:
- https://dev-06484947.okta.com/
- https://dev-06484947-admin.okta.com
How to make okta authenticate less often.
First, change okta session in Chrome from session level to permanent and set a long expiration time. This step is make sure the same session could be used after Chrome is closed and session token will be lost because it lives only inside memory. 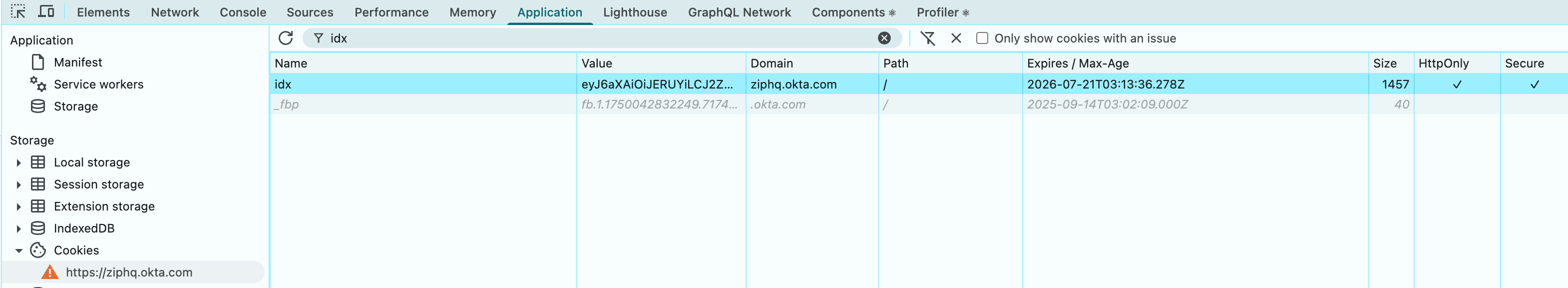 Btw, the max age of a session is 400 days in Chrome. When I tried to set a expiration date beyond that, chrome auto corrected me.
Btw, the max age of a session is 400 days in Chrome. When I tried to set a expiration date beyond that, chrome auto corrected me.
Second, write a cron job to auto refresh the token on the server side.
1
2
3
4
5
6
7
8
9
10
$ curl -L 'https://ziphq.okta.com/api/v1/sessions/me/lifecycle/refresh' -H 'Cookie: idx=<...>'
{
...
"createdAt": "2025-06-16T02:48:21.000Z",
"expiresAt": "2025-06-19T02:48:10.000Z",
"status": "ACTIVE",
...
}
UPDATE!!!
This approach does not work for idx token. See source. Man, I need to be OKTA admin to configure the whole crap.
In principle, I can write a script that read the idx out from Chrome session cookie stored in disk, then use okta sessions/me api to check the expiration status, and use pupeeteer to generate a new token and saves back to Chrome session cookie sqlite database on disk. However, session cookie is encrypted and to encrypt it I need Apple’s Keychain. See this and this. I definitely do not want to save it in plain text in my cron script because if someone cracks my laptop, then he/she may steal my bank account session cookie.
A funny story is that 30 min later after I ran security find-generic-password -w -a Chrome -s 'Chrome Safe Storage', a security guy reached out to me asking what I am doing. :(